Highlights From Confidential Computing 2023
On-Demand Keynotes
Confidential Computing and the Solution to Privacy-Preserving Generative AI

Raluca Ada Popa, Associate Professor, CS, UC Berkeley & Co-founder Opaque Systems
Raluca Ada Popa opens the Summit and discusses the factors driving the considerable rate of growth of the confidential computing market between 2023-2029 including the rise of data privacy laws and the rise of new use cases across every industry. Ada Popa also highlights the recent ground-breaking innovation across every layer of the confidential computing technology stack as well as confidential computing’s position on the larger Privacy Enhancing Technology (PET) landscape & why confidential computing is the next frontier in data security.
Download SlidesThe Mission of the Confidential Computing Consortium and Driving Adoption of Confidential Computing

Mike Bursell, Executive Director, Confidential Computing Consortium
Mike Bursell speaks to the shared mission of the 45+ member organizations in the Confidential Computing Consortium, the CCC’s support of new open source standards and projects relating to confidential computing such as Keystone, Veracruz, Gramine and Occlum and how the CCC helps accelerate the acceptance and adoption of confidential computing.
Download SlidesConfidential Computing and Zero Trust

Vikas Bhatia, Head of Products, Microsoft Azure Confidential Computing
Zero Trust is top of mind for many organizations. Confidential computing supports Zero Trust in ways that can only be accomplished by industry collaboration between chip manufacturers, software platforms, and cloud providers. Learn how this collaboration is extending Zero Trust to data-in-use and letting organizations assume breaches occur in all components outside a tightly controlled and attested trusted computing base.
Download SlidesThe Urgency for Confidential Computing from Zero-Trust Data Clean Rooms to Privacy-Preserving Generative AI


Rishabh Poddar, CEO & Co-founder Opaque Systems
Teresa Tung, Cloud First CTO Accenture
Protecting the confidentiality of organizational data will be discussed and demonstrated by Poddar along with a focus on privacy-preserving generative AI. Poddar also discusses details on how multiple organizations can easily and securely analyze their combined confidential data with Zero Trust Data Clean Rooms without sharing or revealing the underlying raw data. Accenture’s Cloud First Chief Technologist, Teresa Tung, will also share case studies on Opaque’s usage for advanced, collaborative analytics using multi-party data clean rooms.
Download SlidesPanel: Generative AI Security and Privacy

Raluca Ada Popa, Associate Professor, CS, UC Berkeley & Co-founder Opaque Systems
Vikas Bhatia, Head of Product, Azure Confidential Computing (ACC)
Phil Rogers,Compute Server Architect at NVIDIA
Professor Joseph Gonzalez, UC Berkeley
Moderator: Ben Lorica, Host The Data Exchange Podcast, Past: Program Chair of Strataconf.com, TheAIconf.com, and Tensorflow.world.
Overcoming Barriers to Confidential Computing as a Universal Platform

John Manferdelli, Office of the CTO, VMware
Confidential computing provides simple, principled confidentiality and integrity for workloads wherever they run. Within multi-cloud infrastructures, it opens the door for a universal distributed computing solution that addresses verifiable program isolation, programs as authenticated security principals, secure key management, trust management, and the ability to prove these security properties cryptographically "over the wire" to relying parties using attestation. Yet the adoption of confidential computing has been slowed by the difficulty of writing CC-enabled programs quickly and securely, and across hardware technologies. Manferdelli will describe issues and requirements for a universal programming platform and introduce the open source “Certifier Framework for Confidential Computing” that provides a step towards overcoming development barriers.
Download SlidesPanel: Trending Applications and Use Cases in Confidential Computing*

Ron Perez, Fellow, Chief Security Architect, Intel Office of CTO
Nelly Porter, Head of Product, GCP Confidential Computing and Encryption
Vishal Gossain, Practice Leader, Risk Analytics and Strategy, Ernst & Young
Andrew Brust, Moderator, Founder & CEO, Blue Badge Insights
Panelists including experts such as Intel’s Chief Security Architect from Intel’s Office of the CTO, Head of Product, GCP Confidential Computing, and EY experts will discuss practical applications of confidential computing across banking, healthcare, insurance, Blockchain, AdTech, supply chain and more. Panelists will discuss the trends and nuances across use cases, speak to examples, and discuss multi-party computing, confidential AI, multi-party analytics, data clean rooms, and more.
*A. Any views expressed by EY speakers are views of their own, and don't necessarily represent the views of their employers.
B. EY is participating under Chatham house rules.
Confidential Computing as a Cornerstone for Cybersecurity Strategies and Compliance

Xochitl Monteon, Chief Privacy Officer & VP Cybersecurity Risk & Governance, Intel
With the growth of new government-driven cybersecurity strategies and continued expansion of global regulations, organizations are facing increased pressure to transform while still protecting their sensitive data. We will explore how confidential computing technology, rooted in secure clouds and hardware, is uniquely suited today to help organizations meet these new cybersecurity requirements and our vision for tomorrow’s emerging data landscape.
Trusted Execution Environments and Private Messaging

Rolfe Schmidt, Senior Researcher, Signal Messenger
Rolfe works to bring security research into engineering practice at Signal Messenger, the world's most widely used truly private communications app. Keeping metadata private is just as important as protecting message contents, and in some cases it is more important given the intimate details that metadata can expose. Ideally, privacy is accomplished using cryptography to ensure that sensitive data never leaves a user device, but this isn’t always feasible. Attested, confidential TEEs offer another option. This talk will look at how Signal Messenger is using them as one part of a defense-in-depth strategy to offer a fully featured app that provides metadata privacy at a global scale.
Why Organizations Are Investing in Private Multi-Party Analytics

Ion Stoica, Professor UC Berkeley, Executive Chairman, Anyscale, Executive Chairman, Databricks, Board Member Opaque Systems
Ion Stoica, the co-founder of Databricks and Spark open source, co-founder of Anyscale and Ray open source, co-founder of Opaque Systems and co-creator for Spark-based MC2 open source for confidential computing, speaks to the criticality of confidential, private multi-party analytics and machine learning. Stoica highlights why organizations need it, the use cases that demand multi-party analytics and ML, and what's driving the increasing urgency.
Panel: The Surging Demand for Data Clean Rooms. Why Now?

Frank Badalamenti, Partner, Cyber, Risk and Anti-Fraud Technologies, PwC
Rishabh Poddar, CEO, Opaque Systems, Abhishek Chakraborty, Senior Product Manager, MiQ
From media and ad companies, to packaged goods, and marketeers, data clean rooms have become a necessary to ensure data privacy, protect PIIA data and enable collaboration across multiple parties on confidential data. Understand the latest technologies, hear about use cases and find out what’s driving the surging demand.
VMs Are The Next Perimeter

Dr Jethro Beekman, VP Technology & CISO, Fortanix
Hardware manufacturers and infrastructure providers are growing an ever-denser forest of confidential computing options. It can be hard to understand the inherent security improvements offered by each of these. As the constant stream of data breaches in the news shows, perimeter security as a security baseline isn’t cutting it anymore. Trying to secure VM deployments, as commonly used today, directly with confidential computing moves the perimeter but doesn’t fundamentally change the security of data in use. In this talk, we'll look at the pitfalls and what it takes to truly separate security and infrastructure.
Citadel: Side-Channel-Resistant Enclaves on an Open-Source, Speculative, Out-of-Order Processor
Srini Devadas, Webster Professor of EECS, MIT
Citadel is a side-channel-resistant enclave platform running on a speculative, out-of-order, multicore processor with the RISC-V ISA. We developed a new hardware mechanism to prevent enclaves from speculatively accessing shared memory, effectively protecting them from speculative attacks. Our multicore processor runs on an FPGA and boots untrusted Linux. We open-source our end-to-end hardware and software infrastructure in the hope of sparking research and development to bridge the gap between architectural proposals and deployed enclaves.
Download SlidesInnovation and Collaboration at Scale: How Confidential Computing Empowers Enterprises to Fully Embrace the Public Cloud

Ayal Yogev, CEO & Founder, Anjuna Security
Despite the massive benefits of cloud computing, enterprises in strategic sectors such as financial services, healthcare, defense, and government remain hesitant to fully embrace the public cloud. This hesitancy effectively places a glass ceiling on the scale at which innovation and collaboration can occur. Yogev speaks to how the rapid maturation of confidential computing platforms is poised to serve as the catalyst to the next phase of cloud adoption by unlocking unprecedented data security and privacy. In his talk, Ayal will highlight real-world examples of how organizations across industries are already leveraging confidential computing, and demonstrate how doing so ultimately turns a security solution into a vehicle for increased innovation and fearless collaboration.
Download SlidesOn-Demand Track Sessions
To access all of the sessions in a particular track, click on one of the three tracks below.
The Opaque Platform for Secure Multi-party Analytics

Jay Harel, VP, Products, Opaque Systems and Russell Goodwin, Customer Solutions, Opaque Systems
Russell Goodwin, Customer Solutions, Opaque Systems
Use cases across banking, healthcare, AdTech, insurance, manufacturing and more that involve confidential and sensitive data require capabilities for secure inter-company and intra-company collaborative analytics on encrypted data in TEEs while ensuring each party is only privy to the data they own. Learn about Opaque’s unique platform for collaborative, multi-partly analytics and Data Clean Room capabilities and experience it through a live demo.
Enabling Secure Multi-Party Collaboration With Confidential Computing
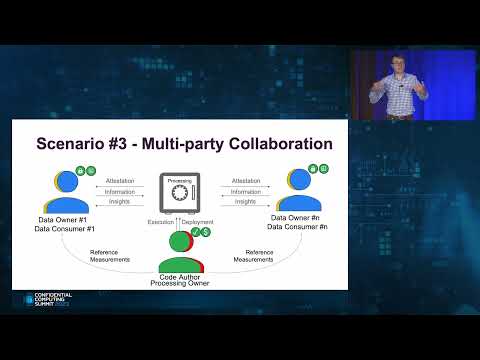
Rene Kolga, Product Manager, Google
Can we create a usable trusted execution environment that supports a trust model where the workload author, workload operator, and resource owners are separate, mutually distrusting parties? Most definitely!
GCP's Confidential Space is a system that uses confidential computing to protect the workload from an untrusted workload operator while providing code and data integrity, and data confidentiality guarantees. This unlocks multiple secure collaboration and privacy-preserving analytics use cases.
Securing Secrets on Edge with SGX Enclaves

Henry Wang, Network Platform Security, Software Engineer, Meta
• Introduction to SGX Enclaves
• Overview of FBEnclave Platform
• Production Use Case on Edge
• Deployment Challenges and Tradeoffs
• Some Performance Benchmarks
An Open Source Certifier Framework for Confidential Computing

John Manferdelli, Office of the CTO, VMware
Ye Li, Staff Engineer, VMware
Confidential computing is a foundational technology, but its adoption has been inhibited by the difficulty in implementing programs quickly even on a single platform. In addition, fragmentation in the TEE platform market has prevented software portability and reuse across TEE technologies. In this session, we will discuss the Certifier Framework for confidential computing, an open source project offering a simple, general API and accompanying service for managing attestation in scaled CC programs. With a half dozen or so API calls, a developer can incorporate CC into their software without deep expertise in security and platform-specific TEE technologies. Furthermore, the framework also decouples trust policy from program code and supports managed deployment. We’ll cover the programming model, trust model and support (including policy and key storage) that makes the Certifier Framework easy to use and broadly applicable.
Download SlidesLowering the Barriers to Confidential Computing

Thomas Fossati, Principal Engineer
Marc Meunier, Director Ecosystem Development, ARM
Providers of computing platforms are racing to deploy products that deliver on the promise of confidential computing. As with any new technology, the initial investment can be high, and pioneers face the risk of cost overrun and failure. In this presentation we explore some of the implementation choices, and the resources Arm is making available to simplify the process of building a platform that supports a “confidential by default” methodology.
Download SlidesBuilding Privacy-Preserving Multi-Party Apps on Azure

Graham Bury, Product Management, Azure Confidential Computing (ACC)
Learn about real-world multiparty computing scenarios enabled by Azure confidential computing, including solutions provided by Microsoft technology partners. Discover new Azure offerings that make it easier to develop privacy-preserving applications, including new confidential container offerings in Azure.
Download SlidesApplication of confidential computing to Anti Money Laundering in Canada*

Vishal Gossain Practice Leader, Risk Analytics and Strategy, Ernst and Young
In Canada, financial institutions face regulatory and privacy challenges in sharing information with each other on their customers to build inter-institution models to better detect money laundering. In collaboration with UC Berkeley (MC2), EY is working with the Big 5 Canadian banks and regulators to create an AML consortium to share data for inter-FI human trafficking detection models. This talk will focus on the consortium framework, technology, progress made, challenges and future outlook.
*1. Any views expressed by speakers are views of their own, and don’t necessarily represent the views of their employers.
2. EY is participating under Chatham house rules.
Confidential Computing in Eyecare

Jackie Sweet, Lead Software Engineer, Dr Tavel Optical Group
How an Indiana eyecare provider is leveraging confidential computing to build a zero trust infrastructure.
Download SlidesAccelerating Confidential Computing Adoption: CCC’s Open Source Project Highlights

Lily Sturmann CCC and Office of the CTO Emerging Technologies, RedHat
The CCC brings together hardware providers, software solutions and cloud providers to ease and accelerate the adoption of confidential computing. Learn also how the CCC embodies open governance and open collaboration, which includes driving commitments from numerous member organizations and actively supporting contributions from several open source projects such as Enarx, Keystone, Gramine, Open Enclave SDK, and many more.
Download SlidesPervasive Confidential Computing From Cloud-to-Edge
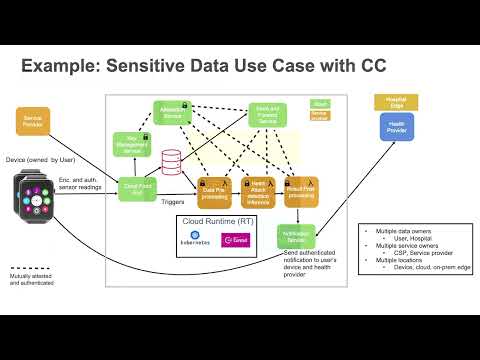
Mona Vij, Principal Engineer, Intel Labs
Security and compliance solutions are not one-size-fits-all, and neither is there only one way to deliver confidential computing (CC). Confidentiality and Integrity can be delivered at the application, container, or VM level, with trust verified via a range of attestation mechanisms. We’ll discuss example usages and deployments for each, and how Intel is uniquely positioned to provide this comprehensive backbone for the underlying infrastructure and services. We’ll also introduce the continued evolution of CC to encompass confidential collaboration and distributed confidential computing.
Download SlidesEnabling Confidential Information Retrieval for Regulatory Compliance
Dr. Richard Searle, Vice President of Confidential Computing, Fortanix
With the continuing expansion of data protection legislation, organizations must ensure compliance with legal obligations and organizational risk and compliance policies. In this session, learn how confidential computing supports controlled access to data for analysts working inside and outside the organizational boundary. The session will provide a contextual overview of the business requirement for confidential information retrieval and details of how confidential computing is being used to protect regulated and classified data. A flexible and scalable architecture will be demonstrated, and comparisons provided to alternative solutions to the use-case requirement. The session will provide essential insights for data analysts, compliance officers, and those seeking to enhance the value of their available data assets.
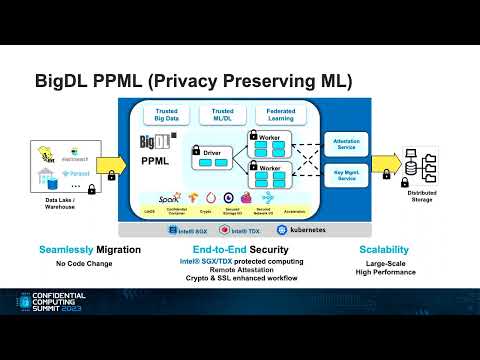
Download SlidesLeveraging SGX/TDX for Secure and Efficient AI at ByteDance using BigDL PPML
Ruide Zhang Security Software Engineer, ByteDance Inc
Jiao Wang, AI Frameworks Engineer, Intel Corporation
While we can safeguard applications and data in memory using Intel SGX (Software Guard Extensions) or TDX (Trust Domain Extensions), ensuring the security of distributed AI workloads remains a complex challenge.
In this session, we will share our experience at ByteDance in developing end-to-end secure AI workloads utilizing Jeddak Sandbox and BigDL PPML. Our solution has been deployed in production for internal customers to build trusted AI applications on large-scale datasets.
Writing Digital Exams secured by Remote Attestation and Cloud Computing

Thore Sommer, Keylime Maintainer, FHNW
Digital exams in schools and universities are getting more and more common. This talk takes a closer look at how we, the University of Applied Sciences and Arts Northwestern Switzerland (FHNW), solved many of the related challenges with Trusted Platform Module (TPM) based remote attestation and cloud computing.
During this session we discuss the solutions that we found and the challenges we faced to implement it in our exam system, the Cloud Assessment Management Platform (CAMPLA).
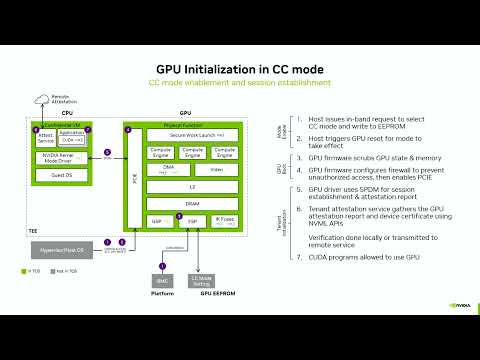
Unlock the Potential of AI with Confidential Computing on NVIDIA GPUs
Philip Rogers, VP System Software, NVIDIA
Confidential computing has made great strides on CPUs over the last several years, especially with the advent of Confidential VMs. This has provided important guarantees for many use cases, but more is needed to run the demanding workloads of Machine Learning and Artificial Intelligence. This session will provide an overview of the software stack and deployment modes for operating the NVIDIA H100 Tensor Core GPU as part of a fully-attested confidential computing platform to deliver the performance levels needed for ML and AI that only GPUs can provide. We will announce the availability of the NVIDIA Confidential Computing Software Stack and how it enables cloud deployments using CVMs, as well as on-premise deployments using Confidential Containers and Kata. confidential computing is a team sport, and we will discuss ongoing collaborations with Microsoft Azure and Intel to advance the confidential computing ecosystem.
Download SlidesFrom a No to On-the-Go! A Frontrunners Story on How We Introduced Confidential Computing in Telco

Jonas De Troy, Domain Manager Public Cloud & Edge, Proximus
The introduction of emerging technologies is always a difficult task in larger sized companies, true for all organisations and relevant for regulated industries. We will articulate a use case to show the process from a no-go - to an on-the-go decision. We will show how technology, vision and legal/compliance need to collaborate to prove added value. As a domain manager for Public Cloud & Edge I had the opportunity to live this process from early concept to how we introduced confidentiality.
Download SlidesWrapping entire Kubernetes clusters into a confidential-computing envelope with Constellation
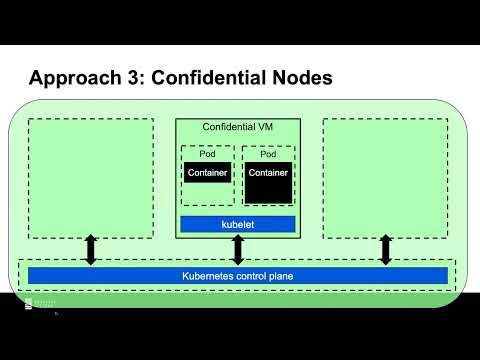
Felix Schuster, CEO, Edgeless Systems
Kubernetes is widely used for managing and scaling containerized workloads and is considered the most popular platform for this purpose. However, for confidential computing to become mainstream, comprehensive confidential-computing features must be brought to Kubernetes.
Download SlidesCollaborative Account Recovery for End-to-End Encryption Systems
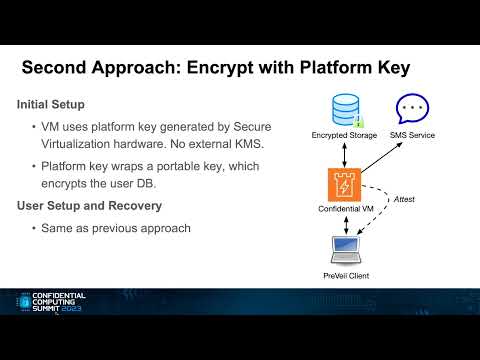
Mike Blaguszewski, Lead Backend Engineer, PreVeil Inc.
In this presentation we will describe method that uses of secure enclaves to recover user keys in Preveil’s end-to-end encrypted system.
Download SlidesCONFIDENTIAL6G EU Research Project

Drasko Draskovic, CEO, Abstract Machines
Dušan Borovčanin, Software Architect, Ultraviolet
CONFIDENTIAL6G is a large-scale European research project, engaging seven academic and research institutes, three industrial partners, and three SMEs. Project develops tools, libraries, mechanisms and architectural blueprints for confidentiality in 6G, confidential computing enablers and TEE software abstraction layer. This talk will describe the project, its concept, objectives, organization and research strategies related to confidential computing subjects.
Download SlidesTEEtime: A New Architecture for Bringing Sovereignty to Smartphones
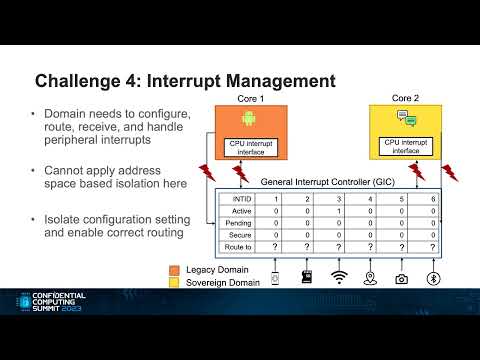
Ivan Puddu, ETH Zurich
Srdjan Capkun, Professor, ETH Zurich
Shweta Shinde, Assistant Professor, ETH Zurich
Phone manufacturers, operators, OS vendors, and users have diverse interests but imbalanced security dynamics. Developers entrust their security to OS vendors who can limit the user, OSes then rely on the firmware for protection.
In this talk, we present a new smartphone architecture called TEEtime that balances the ecosystem while maintaining compatibility. We create ARM TEE-based domains for users and OSes to isolate resources, peripherals, and interrupts as demonstrated with case studies.
Accelerating your digital Business with Anjuna Confidential Computing Platform

Mark Bower, VP Product, Anjuna Security
Confidential computing is driving radical changes in how leading organizations innovate and transform their digital business. Beyond making transformation seamless and secure, it is enabling G2000 enterprises to embrace the cloud at scale, powering optimized digital experiences, privacy-enhanced analytics, and new business models. This session will provide an overview of Anjuna’s platform, how it can be deployed in minutes effectively to secure enterprise workloads without disruption, and how a global financial services organization is leveraging it to accelerate its cloud-first strategy.
Download SlidesCC for AI/ML Models: A Comprehensive Security Framework for In-Use Protection, Ownership, and Data
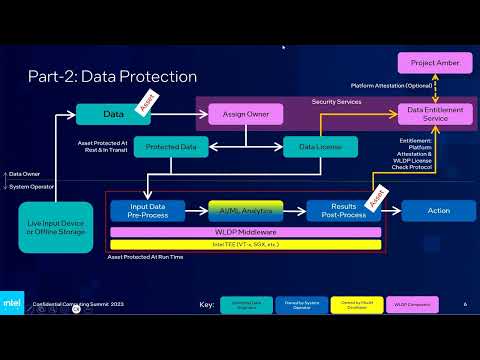
Jay Chetty, Cloud Security Architect, Confidential Computing, Intel
As AI/ML models increase in value and application across sectors, their protection becomes paramount. These models, which often demand substantial investment for training and optimization, face threats of tampering and theft. Furthermore, data used for inference holds significant business value and is often subject to regulations such as GDPR and HIPAA. This AI/ML Security Framework offers a protective layer to these models. It secures models at rest, during transit, and at run time, ensuring integrity, confidentiality, and control over their usage. It introduces model "ownership" and the concept of model licensing, allowing developers to monitor deployment and potentially revoke a model’s use if misbehavior or critical flaws are detected. The framework applies cryptographic techniques and Intel Trusted Execution Environments (TEEs) to protect models. TEE attestation, used in licensing, is facilitated via Secure Boot and Intel Platform Trust Technology or SGX-based DCAP. The model’s protection is extended to data streams used for various AI/ML analytics and output results. Designed for AI/ML specialists with limited security expertise, this framework is delivered with a set of easy-to-use tools and is open-sourced, compatible with Linux KVM (VT-x), Intel SGX (with Gramine), and Kubernetes Containers.
Data Clean Rooms for Secure Multi-Party Collaborative Analytics on Confidential Data

Rishabh Poddar, CEO, Opaque Systems
Confidential collaboration on shared data has forced organizations to make trade-offs and compromises when sharing sensitive data. Learn how Confidential Data Clean Rooms eliminate these trade-offs and provide increased data security, analytic quality, reduced costs, and improved collaboration.
Confidential Containers, Grow Up and Leave the Nest

Amar Gowda, Principal Product Manager, Microsoft
Learn how to deploy confidential pods on public clouds using Cloud API Adaptor (CAA), a sub-project of the Confidential Containers project. This open-source project enables the creation of CVMs on public clouds by integrating with Kubernetes and kata-containers. In this talk, we’ll discuss the technical details of CAA, its integration with k8s, the challenges of deploying pods to k8s using this non-obvious approach, attestation on the respective hardware used to power these virtual machines, etc.
Download SlidesAn Open, Platform-Neutral Approach to Attestation
Mathias Brossard, Principal Security Architect, Arm
Attestation is one of the pillars on which confidential computing rests. A compute environment needs to prove its confidential characteristics before workloads can be executed. Methods of attestation are often platform-specific, leading to fragmentation as more confidential platforms and architectures emerge. This session shows how open-source, platform-neutral, standards-based abstractions can be applied in this space, and invites the community to collaborate and invest in them.
Download SlidesCollaborative Confidential Computing: FHE vs sMPC vs Confidential Computing. Security Models and Real World Use Cases
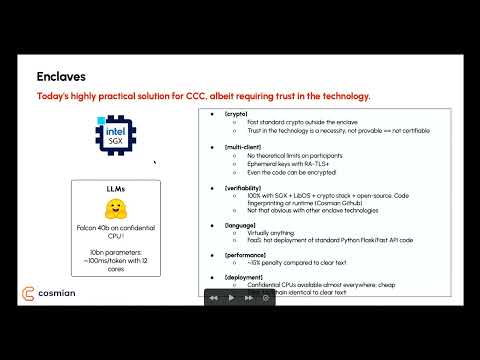
Bruno Grieder, CTO & Co-Founder, Cosmian
Poster Sessions
An Introduction to Huawei Qingtian Enclaves

Quoc Do Le, Confidential Computing Lead, Huawei Munich Research Center
Qingtian Enclave provides a secure and isolated environment for running sensitive workloads and data in the cloud. With QingTian Enclaves, customers can leverage the power of cloud computing in Huawei Cloud while maintaining the confidentiality and integrity of their application.
Cocos AI—System for Confidential Collaborative AI
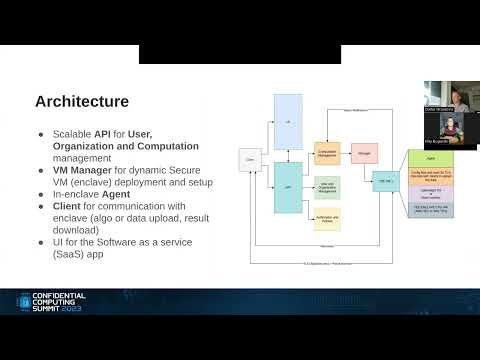
Darko Draskovic, Senior Software Engineer, Ultraviolet
Filip Bugarski, Software Engineer, Ultraviolet
Cocos AI is a cloud distributed microservice-based solution that enables confidential and privacy-preserving AI/ML and allows data scientists to train AI and ML models on confidential data that is never revealed, and can be used for Secure Multi-Party Computation (SMPC).
Achieving Kata Confidential Containers Deployments on Azure for Your Zero Trust Operator Deployments

Amar Gowda, Principal Product Manager, Microsoft
We have Confidential computing with AMD’s SEV-SNP based Trusted Execution Environments (TEE) which provides remote attestation, memory and code protection, isolation from host. Then we have Kata Confidential Containers Open-Source Project that allows you to achieve the highest form of isolation from other pods, host, and Kubernetes components in a single Kubernetes container host. Combining these two can help deliver zero trust operator deployments.



